src/mod/server.mod/servmsg.c File Reference
Go to the source code of this file.
Functions | |
| static int | gotfake433 (char *from) |
| static int | check_tcl_msg (char *cmd, char *nick, char *uhost, struct userrec *u, char *args) |
| static int | check_tcl_msgm (char *cmd, char *nick, char *uhost, struct userrec *u, char *arg) |
| static int | check_tcl_notc (char *nick, char *uhost, struct userrec *u, char *dest, char *arg) |
| static int | check_tcl_raw (char *from, char *code, char *msg) |
| static int | check_tcl_raw4 (char *from, char *code, char *msg, char *tags) |
| static int | check_tcl_ctcpr (char *nick, char *uhost, struct userrec *u, char *dest, char *keyword, char *args, p_tcl_bind_list table) |
| static int | check_tcl_wall (char *from, char *msg) |
| static int | check_tcl_flud (char *nick, char *uhost, struct userrec *u, char *ftype, char *chname) |
| static int | check_tcl_out (int which, char *msg, int sent) |
| static int | match_my_nick (char *nick) |
| static int | got001 (char *from, char *msg) |
| static int | got442 (char *from, char *msg) |
| static void | nuke_server (char *reason) |
| static int | detect_flood (char *floodnick, char *floodhost, char *from, int which) |
| static int | detect_avalanche (char *msg) |
| static int | gotmsg (char *from, char *msg) |
| static int | gotnotice (char *from, char *msg) |
| static int | got251 (char *from, char *msg) |
| static int | gotwall (char *from, char *msg) |
| static void | minutely_checks () |
| static int | gotpong (char *from, char *msg) |
| static void | got303 (char *from, char *msg) |
| static int | got432 (char *from, char *msg) |
| static int | got433 (char *from, char *msg) |
| static int | got437 (char *from, char *msg) |
| static int | got438 (char *from, char *msg) |
| static int | got451 (char *from, char *msg) |
| static int | goterror (char *from, char *msg) |
| static int | gotnick (char *from, char *msg) |
| static int | gotmode (char *from, char *msg) |
| static void | disconnect_server (int idx) |
| static void | eof_server (int idx) |
| static void | display_server (int idx, char *buf) |
| static void | connect_server (void) |
| static void | kill_server (int idx, void *x) |
| static void | timeout_server (int idx) |
| static void | server_activity (int idx, char *msg, int len) |
| static int | gotping (char *from, char *msg) |
| static int | gotkick (char *from, char *msg) |
| static int | whoispenalty (char *from, char *msg) |
| static int | got311 (char *from, char *msg) |
| static int | got465 (char *from, char *msg) |
| static void | server_resolve_success (int) |
| static void | server_resolve_failure (int) |
Variables | |
| static time_t | last_ctcp = (time_t) 0L |
| static int | count_ctcp = 0 |
| static char | altnick_char = 0 |
| static char | ctcp_reply [1024] = "" |
| static int | lastmsgs [3] |
| static char | lastmsghost [3][81] |
| static time_t | lastmsgtime [3] |
| static struct dcc_table | SERVER_SOCKET |
| static cmd_t | my_raw_binds [] |
Function Documentation
| static int check_tcl_ctcpr | ( | char * | nick, | |
| char * | uhost, | |||
| struct userrec * | u, | |||
| char * | dest, | |||
| char * | keyword, | |||
| char * | args, | |||
| p_tcl_bind_list | table | |||
| ) | [static] |
Definition at line 204 of file servmsg.c.
References BIND_EXEC_LOG, BIND_STACKABLE, BIND_USE_ATTR, BIND_WANTRET, check_tcl_bind, FR_ANYWH, FR_CHAN, FR_GLOBAL, get_user_flagrec, H_ctcp, H_ctcr, userrec::handle, interp, MATCH_MASK, and NULL.
00207 { 00208 struct flag_record fr = { FR_GLOBAL | FR_CHAN | FR_ANYWH, 0, 0, 0, 0, 0 }; 00209 int x; 00210 00211 get_user_flagrec(u, &fr, NULL); 00212 Tcl_SetVar(interp, "_ctcpr1", nick, 0); 00213 Tcl_SetVar(interp, "_ctcpr2", uhost, 0); 00214 Tcl_SetVar(interp, "_ctcpr3", u ? u->handle : "*", 0); 00215 Tcl_SetVar(interp, "_ctcpr4", dest, 0); 00216 Tcl_SetVar(interp, "_ctcpr5", keyword, 0); 00217 Tcl_SetVar(interp, "_ctcpr6", args, 0); 00218 x = check_tcl_bind(table, keyword, &fr, 00219 " $_ctcpr1 $_ctcpr2 $_ctcpr3 $_ctcpr4 $_ctcpr5 $_ctcpr6", 00220 MATCH_MASK | BIND_USE_ATTR | BIND_STACKABLE | 00221 ((table == H_ctcp) ? BIND_WANTRET : 0)); 00222 return (x == BIND_EXEC_LOG) || (table == H_ctcr); 00223 }
| static int check_tcl_flud | ( | char * | nick, | |
| char * | uhost, | |||
| struct userrec * | u, | |||
| char * | ftype, | |||
| char * | chname | |||
| ) | [static] |
Definition at line 247 of file servmsg.c.
References BIND_EXEC_LOG, BIND_STACKABLE, BIND_WANTRET, check_tcl_bind, H_flud, userrec::handle, interp, and MATCH_MASK.
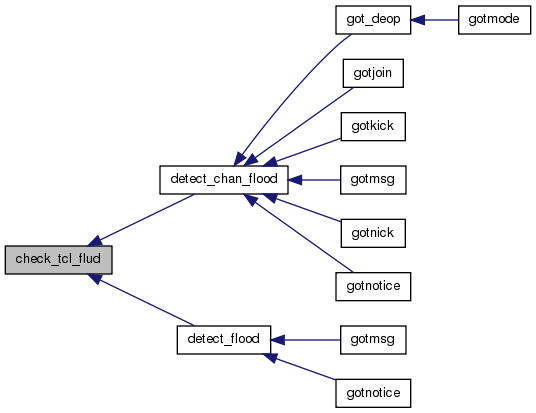
Referenced by detect_chan_flood(), and detect_flood().
00249 { 00250 int x; 00251 00252 Tcl_SetVar(interp, "_flud1", nick, 0); 00253 Tcl_SetVar(interp, "_flud2", uhost, 0); 00254 Tcl_SetVar(interp, "_flud3", u ? u->handle : "*", 0); 00255 Tcl_SetVar(interp, "_flud4", ftype, 0); 00256 Tcl_SetVar(interp, "_flud5", chname, 0); 00257 x = check_tcl_bind(H_flud, ftype, 0, 00258 " $_flud1 $_flud2 $_flud3 $_flud4 $_flud5", 00259 MATCH_MASK | BIND_STACKABLE | BIND_WANTRET); 00260 return (x == BIND_EXEC_LOG); 00261 }
| static int check_tcl_msg | ( | char * | cmd, | |
| char * | nick, | |||
| char * | uhost, | |||
| struct userrec * | u, | |||
| char * | args | |||
| ) | [static] |
Definition at line 96 of file servmsg.c.
References BIND_EXEC_LOG, BIND_EXECUTED, BIND_HAS_BUILTINS, BIND_MATCHED, BIND_USE_ATTR, check_tcl_bind, FR_ANYWH, FR_CHAN, FR_GLOBAL, get_user_flagrec, H_msg, userrec::handle, interp, LOG_CMDS, MATCH_EXACT, NULL, and putlog.
Referenced by gotmsg().
00098 { 00099 struct flag_record fr = { FR_GLOBAL | FR_CHAN | FR_ANYWH, 0, 0, 0, 0, 0 }; 00100 char *hand = u ? u->handle : "*"; 00101 int x; 00102 00103 get_user_flagrec(u, &fr, NULL); 00104 Tcl_SetVar(interp, "_msg1", nick, 0); 00105 Tcl_SetVar(interp, "_msg2", uhost, 0); 00106 Tcl_SetVar(interp, "_msg3", hand, 0); 00107 Tcl_SetVar(interp, "_msg4", args, 0); 00108 x = check_tcl_bind(H_msg, cmd, &fr, " $_msg1 $_msg2 $_msg3 $_msg4", 00109 MATCH_EXACT | BIND_HAS_BUILTINS | BIND_USE_ATTR); 00110 if (x == BIND_EXEC_LOG) 00111 putlog(LOG_CMDS, "*", "(%s!%s) !%s! %s %s", nick, uhost, hand, cmd, args); 00112 return ((x == BIND_MATCHED) || (x == BIND_EXECUTED) || (x == BIND_EXEC_LOG)); 00113 }
| static int check_tcl_msgm | ( | char * | cmd, | |
| char * | nick, | |||
| char * | uhost, | |||
| struct userrec * | u, | |||
| char * | arg | |||
| ) | [static] |
Definition at line 115 of file servmsg.c.
References BIND_EXEC_LOG, BIND_NOMATCH, BIND_STACKABLE, BIND_STACKRET, BIND_USE_ATTR, check_tcl_bind, FR_ANYWH, FR_CHAN, FR_GLOBAL, get_user_flagrec, H_msgm, userrec::handle, interp, MATCH_MASK, NULL, and simple_sprintf.
Referenced by gotmsg().
00117 { 00118 struct flag_record fr = { FR_GLOBAL | FR_CHAN | FR_ANYWH, 0, 0, 0, 0, 0 }; 00119 int x; 00120 char args[1024]; 00121 00122 if (arg[0]) 00123 simple_sprintf(args, "%s %s", cmd, arg); 00124 else 00125 strcpy(args, cmd); 00126 get_user_flagrec(u, &fr, NULL); 00127 Tcl_SetVar(interp, "_msgm1", nick, 0); 00128 Tcl_SetVar(interp, "_msgm2", uhost, 0); 00129 Tcl_SetVar(interp, "_msgm3", u ? u->handle : "*", 0); 00130 Tcl_SetVar(interp, "_msgm4", args, 0); 00131 x = check_tcl_bind(H_msgm, args, &fr, " $_msgm1 $_msgm2 $_msgm3 $_msgm4", 00132 MATCH_MASK | BIND_USE_ATTR | BIND_STACKABLE | BIND_STACKRET); 00133 00134 /* 00135 * 0 - no match 00136 * 1 - match, log 00137 * 2 - match, don't log 00138 */ 00139 if (x == BIND_NOMATCH) 00140 return 0; 00141 if (x == BIND_EXEC_LOG) 00142 return 2; 00143 00144 return 1; 00145 }
| static int check_tcl_notc | ( | char * | nick, | |
| char * | uhost, | |||
| struct userrec * | u, | |||
| char * | dest, | |||
| char * | arg | |||
| ) | [static] |
Definition at line 147 of file servmsg.c.
References BIND_EXEC_LOG, BIND_NOMATCH, BIND_STACKABLE, BIND_STACKRET, BIND_USE_ATTR, check_tcl_bind, FR_ANYWH, FR_CHAN, FR_GLOBAL, get_user_flagrec, H_notc, userrec::handle, interp, MATCH_MASK, and NULL.
Referenced by gotnotice().
00149 { 00150 struct flag_record fr = { FR_GLOBAL | FR_CHAN | FR_ANYWH, 0, 0, 0, 0, 0 }; 00151 int x; 00152 00153 get_user_flagrec(u, &fr, NULL); 00154 Tcl_SetVar(interp, "_notc1", nick, 0); 00155 Tcl_SetVar(interp, "_notc2", uhost, 0); 00156 Tcl_SetVar(interp, "_notc3", u ? u->handle : "*", 0); 00157 Tcl_SetVar(interp, "_notc4", arg, 0); 00158 Tcl_SetVar(interp, "_notc5", dest, 0); 00159 x = check_tcl_bind(H_notc, arg, &fr, " $_notc1 $_notc2 $_notc3 $_notc4 $_notc5", 00160 MATCH_MASK | BIND_USE_ATTR | BIND_STACKABLE | BIND_STACKRET); 00161 00162 /* 00163 * 0 - no match 00164 * 1 - match, log 00165 * 2 - match, don't log 00166 */ 00167 if (x == BIND_NOMATCH) 00168 return 0; 00169 if (x == BIND_EXEC_LOG) 00170 return 2; 00171 00172 return 1; 00173 }
| static int check_tcl_out | ( | int | which, | |
| char * | msg, | |||
| int | sent | |||
| ) | [static] |
Definition at line 263 of file servmsg.c.
References BIND_EXEC_LOG, BIND_STACKABLE, BIND_WANTRET, check_tcl_bind, DP_HELP, DP_HELP_NEXT, DP_MODE, DP_MODE_NEXT, DP_SERVER, DP_SERVER_NEXT, H_out, interp, and MATCH_MASK.
Referenced by deq_kick(), deq_msg(), fast_deq(), and queue_server().
00264 { 00265 int x; 00266 char args[32], *queue; 00267 00268 switch (which) { 00269 case DP_MODE: 00270 case DP_MODE_NEXT: 00271 queue = "mode"; 00272 break; 00273 case DP_SERVER: 00274 case DP_SERVER_NEXT: 00275 queue = "server"; 00276 break; 00277 case DP_HELP: 00278 case DP_HELP_NEXT: 00279 queue = "help"; 00280 break; 00281 default: 00282 queue = "noqueue"; 00283 } 00284 snprintf(args, sizeof args, "%s %s", queue, sent ? "sent" : "queued"); 00285 Tcl_SetVar(interp, "_out1", queue, 0); 00286 Tcl_SetVar(interp, "_out2", msg, 0); 00287 Tcl_SetVar(interp, "_out3", sent ? "sent" : "queued", 0); 00288 x = check_tcl_bind(H_out, args, 0, " $_out1 $_out2 $_out3", 00289 MATCH_MASK | BIND_STACKABLE | BIND_WANTRET); 00290 00291 return (x == BIND_EXEC_LOG); 00292 }
| static int check_tcl_raw | ( | char * | from, | |
| char * | code, | |||
| char * | msg | |||
| ) | [static] |
Definition at line 175 of file servmsg.c.
References BIND_EXEC_LOG, BIND_STACKABLE, BIND_WANTRET, check_tcl_bind, H_raw, interp, and MATCH_EXACT.
Referenced by server_activity().
00176 { 00177 int x; 00178 00179 Tcl_SetVar(interp, "_raw1", from, 0); 00180 Tcl_SetVar(interp, "_raw2", code, 0); 00181 Tcl_SetVar(interp, "_raw3", msg, 0); 00182 x = check_tcl_bind(H_raw, code, 0, " $_raw1 $_raw2 $_raw3", 00183 MATCH_EXACT | BIND_STACKABLE | BIND_WANTRET); 00184 00185 /* Return 1 if processed */ 00186 return (x == BIND_EXEC_LOG); 00187 }

| static int check_tcl_raw4 | ( | char * | from, | |
| char * | code, | |||
| char * | msg, | |||
| char * | tags | |||
| ) | [static] |
Definition at line 189 of file servmsg.c.
References BIND_EXEC_LOG, BIND_STACKABLE, BIND_WANTRET, check_tcl_bind, H_raw, interp, and MATCH_EXACT.
Referenced by server_activity().
00190 { 00191 int x; 00192 00193 Tcl_SetVar(interp, "_raw1", from, 0); 00194 Tcl_SetVar(interp, "_raw2", code, 0); 00195 Tcl_SetVar(interp, "_raw3", msg, 0); 00196 Tcl_SetVar(interp, "_raw4", tags, 0); 00197 x = check_tcl_bind(H_raw, code, 0, " $_raw1 $_raw2 $_raw3 $_raw4", 00198 MATCH_EXACT | BIND_STACKABLE | BIND_WANTRET); 00199 00200 /* Return 1 if processed */ 00201 return (x == BIND_EXEC_LOG); 00202 }

| static int check_tcl_wall | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 225 of file servmsg.c.
References BIND_EXEC_LOG, BIND_NOMATCH, BIND_STACKABLE, BIND_STACKRET, check_tcl_bind, H_wall, interp, and MATCH_MASK.
Referenced by gotwall().
00226 { 00227 int x; 00228 00229 Tcl_SetVar(interp, "_wall1", from, 0); 00230 Tcl_SetVar(interp, "_wall2", msg, 0); 00231 x = check_tcl_bind(H_wall, msg, 0, " $_wall1 $_wall2", 00232 MATCH_MASK | BIND_STACKABLE | BIND_STACKRET); 00233 00234 /* 00235 * 0 - no match 00236 * 1 - match, log 00237 * 2 - match, don't log 00238 */ 00239 if (x == BIND_NOMATCH) 00240 return 0; 00241 if (x == BIND_EXEC_LOG) 00242 return 2; 00243 00244 return 1; 00245 }
| static void connect_server | ( | void | ) | [static] |
Definition at line 1294 of file servmsg.c.
References botuserhost, CHAN_JUPED, chanset, check_tcl_event, connectserver, curserv, cycle_time, dcc, dcc_dnsipbyhost, DCC_DNSWAIT, do_tcl, empty_msgq(), get_data_ptr, IRC_SERVERTRY, lastpingcheck, LOG_SERV, never_give_up, new_dcc, newserver, newserverpass, newserverport, chanset_t::next, next_server(), nick_juped, now, putlog, RES_IPBYHOST, resolvserv, server_cycle_wait, serverlist, chanset_t::status, strncpyz, trying_server, and UHOSTLEN.
Referenced by server_secondly().
01295 { 01296 char pass[121], botserver[UHOSTLEN]; 01297 static int oldserv = -1; 01298 int servidx; 01299 unsigned int botserverport = 0; 01300 01301 lastpingcheck = 0; 01302 trying_server = now; 01303 empty_msgq(); 01304 /* Start up the counter (always reset it if "never-give-up" is on) */ 01305 if ((oldserv < 0) || (never_give_up)) 01306 oldserv = curserv; 01307 if (newserverport) { /* Jump to specified server */ 01308 curserv = -1; /* Reset server list */ 01309 strcpy(botserver, newserver); 01310 botserverport = newserverport; 01311 strcpy(pass, newserverpass); 01312 newserver[0] = 0; 01313 newserverport = 0; 01314 newserverpass[0] = 0; 01315 oldserv = -1; 01316 } else { 01317 if (curserv == -1) 01318 curserv = 999; 01319 pass[0] = 0; 01320 } 01321 if (!cycle_time) { 01322 struct chanset_t *chan; 01323 struct server_list *x = serverlist; 01324 01325 if (!x && !botserverport) { 01326 putlog(LOG_SERV, "*", "No servers in server list"); 01327 cycle_time = 300; 01328 return; 01329 } 01330 01331 servidx = new_dcc(&DCC_DNSWAIT, sizeof(struct dns_info)); 01332 if (servidx < 0) { 01333 putlog(LOG_SERV, "*", 01334 "NO MORE DCC CONNECTIONS -- Can't create server connection."); 01335 return; 01336 } 01337 01338 if (connectserver[0]) /* drummer */ 01339 do_tcl("connect-server", connectserver); 01340 check_tcl_event("connect-server"); 01341 next_server(&curserv, botserver, &botserverport, pass); 01342 putlog(LOG_SERV, "*", "%s %s:%d", IRC_SERVERTRY, botserver, botserverport); 01343 01344 dcc[servidx].port = botserverport; 01345 strcpy(dcc[servidx].nick, "(server)"); 01346 strncpyz(dcc[servidx].host, botserver, UHOSTLEN); 01347 01348 botuserhost[0] = 0; 01349 01350 nick_juped = 0; 01351 for (chan = chanset; chan; chan = chan->next) 01352 chan->status &= ~CHAN_JUPED; 01353 01354 dcc[servidx].timeval = now; 01355 dcc[servidx].sock = -1; 01356 dcc[servidx].u.dns->host = get_data_ptr(strlen(dcc[servidx].host) + 1); 01357 strcpy(dcc[servidx].u.dns->host, dcc[servidx].host); 01358 dcc[servidx].u.dns->cbuf = get_data_ptr(strlen(pass) + 1); 01359 strcpy(dcc[servidx].u.dns->cbuf, pass); 01360 dcc[servidx].u.dns->dns_success = server_resolve_success; 01361 dcc[servidx].u.dns->dns_failure = server_resolve_failure; 01362 dcc[servidx].u.dns->dns_type = RES_IPBYHOST; 01363 dcc[servidx].u.dns->type = &SERVER_SOCKET; 01364 01365 if (server_cycle_wait) 01366 /* Back to 1st server & set wait time. 01367 * Note: Put it here, just in case the server quits on us quickly 01368 */ 01369 cycle_time = server_cycle_wait; 01370 else 01371 cycle_time = 0; 01372 01373 /* I'm resolving... don't start another server connect request */ 01374 resolvserv = 1; 01375 /* Resolve the hostname. */ 01376 dcc_dnsipbyhost(dcc[servidx].host); 01377 } 01378 }
| static int detect_avalanche | ( | char * | msg | ) | [static] |
Definition at line 486 of file servmsg.c.
References count.
Referenced by gotmsg(), and gotnotice().
00487 { 00488 int count = 0; 00489 unsigned char *p; 00490 00491 for (p = (unsigned char *) msg; (*p) && (count < 8); p++) 00492 if ((*p == 7) || (*p == 1)) 00493 count++; 00494 if (count >= 8) 00495 return 1; 00496 else 00497 return 0; 00498 }
| static int detect_flood | ( | char * | floodnick, | |
| char * | floodhost, | |||
| char * | from, | |||
| int | which | |||
| ) | [static] |
Definition at line 411 of file servmsg.c.
References addignore, botnetnick, botuserhost, check_tcl_flud(), egg_strcasecmp, userrec::flags, FLOOD_CTCP, FLOOD_NOTICE, FLOOD_PRIVMSG, flud_ctcp_thr, flud_ctcp_time, flud_thr, flud_time, get_user_by_host, ignore_time, IRC_FLOODIGNORE1, lastmsghost, lastmsgs, lastmsgtime, LOG_MISC, match_my_nick(), now, putlog, simple_sprintf, USER_BOT, and USER_FRIEND.
Referenced by gotmsg(), and gotnotice().
00412 { 00413 char *p, ftype[10], h[1024]; 00414 struct userrec *u; 00415 int thr = 0, lapse = 0, atr; 00416 00417 /* Okay, make sure i'm not flood-checking myself */ 00418 if (match_my_nick(floodnick)) 00419 return 0; 00420 00421 /* My user@host (?) */ 00422 if (!egg_strcasecmp(floodhost, botuserhost)) 00423 return 0; 00424 00425 u = get_user_by_host(from); 00426 atr = u ? u->flags : 0; 00427 if (atr & (USER_BOT | USER_FRIEND)) 00428 return 0; 00429 00430 /* Determine how many are necessary to make a flood */ 00431 switch (which) { 00432 case FLOOD_PRIVMSG: 00433 case FLOOD_NOTICE: 00434 thr = flud_thr; 00435 lapse = flud_time; 00436 strcpy(ftype, "msg"); 00437 break; 00438 case FLOOD_CTCP: 00439 thr = flud_ctcp_thr; 00440 lapse = flud_ctcp_time; 00441 strcpy(ftype, "ctcp"); 00442 break; 00443 } 00444 if ((thr == 0) || (lapse == 0)) 00445 return 0; /* No flood protection */ 00446 00447 p = strchr(floodhost, '@'); 00448 if (p) { 00449 p++; 00450 if (egg_strcasecmp(lastmsghost[which], p)) { /* New */ 00451 strcpy(lastmsghost[which], p); 00452 lastmsgtime[which] = now; 00453 lastmsgs[which] = 0; 00454 return 0; 00455 } 00456 } else 00457 return 0; /* Uh... whatever. */ 00458 00459 if (lastmsgtime[which] < now - lapse) { 00460 /* Flood timer expired, reset it */ 00461 lastmsgtime[which] = now; 00462 lastmsgs[which] = 0; 00463 return 0; 00464 } 00465 lastmsgs[which]++; 00466 if (lastmsgs[which] >= thr) { /* FLOOD */ 00467 /* Reset counters */ 00468 lastmsgs[which] = 0; 00469 lastmsgtime[which] = 0; 00470 lastmsghost[which][0] = 0; 00471 u = get_user_by_host(from); 00472 if (check_tcl_flud(floodnick, floodhost, u, ftype, "*")) 00473 return 0; 00474 /* Private msg */ 00475 simple_sprintf(h, "*!*@%s", p); 00476 putlog(LOG_MISC, "*", IRC_FLOODIGNORE1, p); 00477 addignore(h, botnetnick, (which == FLOOD_CTCP) ? "CTCP flood" : 00478 "MSG/NOTICE flood", now + (60 * ignore_time)); 00479 } 00480 return 0; 00481 }
| static void disconnect_server | ( | int | idx | ) | [static] |
Definition at line 1061 of file servmsg.c.
References botuserhost, check_tcl_event, dcc, killsock, nfree, realservername, serv, and server_online.
Referenced by eof_server(), kill_server(), nuke_server(), and timeout_server().
01062 { 01063 if (server_online > 0) 01064 check_tcl_event("disconnect-server"); 01065 server_online = 0; 01066 if (realservername) 01067 nfree(realservername); 01068 realservername = 0; 01069 if (dcc[idx].sock >= 0) 01070 killsock(dcc[idx].sock); 01071 dcc[idx].sock = -1; 01072 serv = -1; 01073 botuserhost[0] = 0; 01074 }
| static void display_server | ( | int | idx, | |
| char * | buf | |||
| ) | [static] |
Definition at line 1083 of file servmsg.c.
References server_lag, and trying_server.
01084 { 01085 sprintf(buf, "%s (lag: %d)", trying_server ? "conn" : "serv", server_lag); 01086 }
| static void eof_server | ( | int | idx | ) | [static] |
Definition at line 1076 of file servmsg.c.
References dcc, disconnect_server(), IRC_DISCONNECTED, LOG_SERV, lostdcc, and putlog.
01077 { 01078 putlog(LOG_SERV, "*", "%s %s", IRC_DISCONNECTED, dcc[idx].host); 01079 disconnect_server(idx); 01080 lostdcc(idx); 01081 }
| static int got001 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 302 of file servmsg.c.
References altnick_char, botname, CHAN_ACTIVE, CHAN_PEND, chanset_t::channel, channel_inactive, chanset, check_tcl_event, curserv, chanset_t::dname, do_tcl, DP_SERVER, dprintf, fixcolon, initserver, chan_t::key, chanset_t::key_prot, LOG_MISC, module_find, chanset_t::name, chanset_t::next, server_list::next, nfree, NICKLEN, nmalloc, now, putlog, realservername, server_online, serverlist, chanset_t::status, and strncpyz.
00303 { 00304 int i; 00305 char *key; 00306 struct chanset_t *chan; 00307 struct server_list *x = serverlist; 00308 00309 /* FIXME - x should never be NULL anywhere in this function, but 00310 * apparently it sometimes is. */ 00311 if (x) { 00312 for (i = curserv; i > 0 && x; i--) 00313 x = x->next; 00314 if (!x) { 00315 putlog(LOG_MISC, "*", "Invalid server list!"); 00316 } else { 00317 if (x->realname) 00318 nfree(x->realname); 00319 x->realname = nmalloc(strlen(from) + 1); 00320 strcpy(x->realname, from); 00321 } 00322 if (realservername) 00323 nfree(realservername); 00324 realservername = nmalloc(strlen(from) + 1); 00325 strcpy(realservername, from); 00326 } else 00327 putlog(LOG_MISC, "*", "No server list!"); 00328 00329 server_online = now; 00330 fixcolon(msg); 00331 strncpyz(botname, msg, NICKLEN); 00332 altnick_char = 0; 00333 dprintf(DP_SERVER, "WHOIS %s\n", botname); /* get user@host */ 00334 if (initserver[0]) 00335 do_tcl("init-server", initserver); /* Call Tcl init-server */ 00336 check_tcl_event("init-server"); 00337 00338 if (!x) 00339 return 0; 00340 00341 if (module_find("irc", 0, 0)) { /* Only join if the IRC module is loaded. */ 00342 for (chan = chanset; chan; chan = chan->next) { 00343 chan->status &= ~(CHAN_ACTIVE | CHAN_PEND); 00344 if (!channel_inactive(chan)) { 00345 00346 key = chan->channel.key[0] ? chan->channel.key : chan->key_prot; 00347 if (key[0]) 00348 dprintf(DP_SERVER, "JOIN %s %s\n", 00349 chan->name[0] ? chan->name : chan->dname, key); 00350 else 00351 dprintf(DP_SERVER, "JOIN %s\n", 00352 chan->name[0] ? chan->name : chan->dname); 00353 } 00354 } 00355 } 00356 00357 return 0; 00358 }
| static int got251 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 745 of file servmsg.c.
References fixcolon, IRC_AUTOJUMP, IRC_CHANGINGSERV, LOG_SERV, min_servs, newsplit, nuke_server(), and putlog.
00746 { 00747 int i; 00748 char *servs; 00749 00750 if (min_servs == 0) 00751 return 0; /* No minimum limit on servers */ 00752 newsplit(&msg); 00753 fixcolon(msg); /* NOTE!!! If servlimit is not set or is 0 */ 00754 for (i = 0; i < 8; i++) 00755 newsplit(&msg); /* lusers IS NOT SENT AT ALL!! */ 00756 servs = newsplit(&msg); 00757 if (strncmp(msg, "servers", 7)) 00758 return 0; /* Was invalid format */ 00759 while (*servs && (*servs < 32)) 00760 servs++; /* I've seen some lame nets put bolds & 00761 * stuff in here :/ */ 00762 i = atoi(servs); 00763 if (i < min_servs) { 00764 putlog(LOG_SERV, "*", IRC_AUTOJUMP, min_servs, i); 00765 nuke_server(IRC_CHANGINGSERV); 00766 } 00767 return 0; 00768 }
| static void got303 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 846 of file servmsg.c.
References botname, DP_SERVER, dprintf, fixcolon, get_altbotnick(), IRC_GETALTNICK, IRC_GETORIGNICK, keepnick, LOG_MISC, newsplit, nick_juped, origbotname, putlog, and rfc_casecmp.
00847 { 00848 char *tmp, *alt; 00849 int ison_orig = 0, ison_alt = 0; 00850 00851 if (!keepnick || !strncmp(botname, origbotname, strlen(botname))) { 00852 return; 00853 } 00854 newsplit(&msg); 00855 fixcolon(msg); 00856 alt = get_altbotnick(); 00857 tmp = newsplit(&msg); 00858 if (tmp[0] && !rfc_casecmp(botname, tmp)) { 00859 while ((tmp = newsplit(&msg))[0]) { /* no, it's NOT == */ 00860 if (!rfc_casecmp(tmp, origbotname)) 00861 ison_orig = 1; 00862 else if (alt[0] && !rfc_casecmp(tmp, alt)) 00863 ison_alt = 1; 00864 } 00865 if (!ison_orig) { 00866 if (!nick_juped) 00867 putlog(LOG_MISC, "*", IRC_GETORIGNICK, origbotname); 00868 dprintf(DP_SERVER, "NICK %s\n", origbotname); 00869 } else if (alt[0] && !ison_alt && rfc_casecmp(botname, alt)) { 00870 putlog(LOG_MISC, "*", IRC_GETALTNICK, alt); 00871 dprintf(DP_SERVER, "NICK %s\n", alt); 00872 } 00873 } 00874 }
| static int got311 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 1226 of file servmsg.c.
References botuserhost, egg_snprintf, match_my_nick(), and newsplit.
01227 { 01228 char *n1, *n2, *u, *h; 01229 01230 n1 = newsplit(&msg); 01231 n2 = newsplit(&msg); 01232 u = newsplit(&msg); 01233 h = newsplit(&msg); 01234 01235 if (!n1 || !n2 || !u || !h) 01236 return 0; 01237 01238 if (match_my_nick(n2)) 01239 egg_snprintf(botuserhost, sizeof botuserhost, "%s@%s", u, h); 01240 01241 return 0; 01242 }
| static int got432 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 878 of file servmsg.c.
References botname, DP_MODE, dprintf, IRC_BADBOTNICK, keepnick, LOG_MISC, makepass, newsplit, NICKMAX, putlog, and server_online.
00879 { 00880 char *erroneus; 00881 00882 newsplit(&msg); 00883 erroneus = newsplit(&msg); 00884 if (server_online) 00885 putlog(LOG_MISC, "*", "NICK IS INVALID: %s (keeping '%s').", erroneus, 00886 botname); 00887 else { 00888 putlog(LOG_MISC, "*", IRC_BADBOTNICK); 00889 if (!keepnick) { 00890 makepass(erroneus); 00891 erroneus[NICKMAX] = 0; 00892 dprintf(DP_MODE, "NICK %s\n", erroneus); 00893 } 00894 return 0; 00895 } 00896 return 0; 00897 }
| static int got433 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 902 of file servmsg.c.
References botname, gotfake433(), LOG_MISC, newsplit, nick_juped, putlog, and server_online.
00903 { 00904 char *tmp; 00905 00906 if (server_online) { 00907 /* We are online and have a nickname, we'll keep it */ 00908 newsplit(&msg); 00909 tmp = newsplit(&msg); 00910 putlog(LOG_MISC, "*", "NICK IN USE: %s (keeping '%s').", tmp, botname); 00911 nick_juped = 0; 00912 return 0; 00913 } 00914 gotfake433(from); 00915 return 0; 00916 }
| static int got437 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 920 of file servmsg.c.
References botname, CHAN_ACTIVE, CHAN_JUPED, CHANMETA, channel_juped, findchan, gotfake433(), IRC_BOTNICKJUPED, IRC_CANTCHANGENICK, IRC_CHANNELJUPED, LOG_MISC, newsplit, nick_juped, NULL, origbotname, putlog, rfc_casecmp, server_online, and chanset_t::status.
00921 { 00922 char *s; 00923 struct chanset_t *chan; 00924 00925 newsplit(&msg); 00926 s = newsplit(&msg); 00927 if (s[0] && (strchr(CHANMETA, s[0]) != NULL)) { 00928 chan = findchan(s); 00929 if (chan) { 00930 if (chan->status & CHAN_ACTIVE) { 00931 putlog(LOG_MISC, "*", IRC_CANTCHANGENICK, s); 00932 } else { 00933 if (!channel_juped(chan)) { 00934 putlog(LOG_MISC, "*", IRC_CHANNELJUPED, s); 00935 chan->status |= CHAN_JUPED; 00936 } 00937 } 00938 } 00939 } else if (server_online) { 00940 if (!nick_juped) 00941 putlog(LOG_MISC, "*", "NICK IS JUPED: %s (keeping '%s').", s, botname); 00942 if (!rfc_casecmp(s, origbotname)) 00943 nick_juped = 1; 00944 } else { 00945 putlog(LOG_MISC, "*", "%s: %s", IRC_BOTNICKJUPED, s); 00946 gotfake433(from); 00947 } 00948 return 0; 00949 }
| static int got438 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
| static int got442 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 362 of file servmsg.c.
References CHAN_ACTIVE, chanset_t::channel, CHANNEL_CLEAR, channel_inactive, DP_SERVER, dprintf, egg_strcasecmp, findchan, _module_entry::funcs, IRC_SERVNOTONCHAN, chan_t::key, chanset_t::key_prot, LOG_MISC, module_find, chanset_t::name, newsplit, putlog, realservername, and chanset_t::status.
00363 { 00364 char *chname, *key; 00365 struct chanset_t *chan; 00366 00367 if (!realservername || egg_strcasecmp(from, realservername)) 00368 return 0; 00369 newsplit(&msg); 00370 chname = newsplit(&msg); 00371 chan = findchan(chname); 00372 if (chan && !channel_inactive(chan)) { 00373 module_entry *me = module_find("channels", 0, 0); 00374 00375 putlog(LOG_MISC, chname, IRC_SERVNOTONCHAN, chname); 00376 if (me && me->funcs) 00377 (me->funcs[CHANNEL_CLEAR]) (chan, 1); 00378 chan->status &= ~CHAN_ACTIVE; 00379 00380 key = chan->channel.key[0] ? chan->channel.key : chan->key_prot; 00381 if (key[0]) 00382 dprintf(DP_SERVER, "JOIN %s %s\n", chan->name, key); 00383 else 00384 dprintf(DP_SERVER, "JOIN %s\n", chan->name); 00385 } 00386 return 0; 00387 }
| static int got451 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 962 of file servmsg.c.
References IRC_NOTREGISTERED1, IRC_NOTREGISTERED2, LOG_MISC, nuke_server(), and putlog.
00963 { 00964 /* Usually if we get this then we really messed up somewhere 00965 * or this is a non-standard server, so we log it and kill the socket 00966 * hoping the next server will work :) -poptix 00967 */ 00968 /* Um, this does occur on a lagged anti-spoof server connection if the 00969 * (minutely) sending of joins occurs before the bot does its ping reply. 00970 * Probably should do something about it some time - beldin 00971 */ 00972 putlog(LOG_MISC, "*", IRC_NOTREGISTERED1, from); 00973 nuke_server(IRC_NOTREGISTERED2); 00974 return 0; 00975 }
| static int got465 | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 1248 of file servmsg.c.
References fixcolon, LOG_SERV, newsplit, nuke_server(), and putlog.
01249 { 01250 newsplit(&msg); /* 465 */ 01251 newsplit(&msg); /* nick */ 01252 01253 fixcolon(msg); 01254 01255 putlog(LOG_SERV, "*", "Server (%s) says I'm banned: %s", from, msg); 01256 putlog(LOG_SERV, "*", "Disconnecting from server."); 01257 nuke_server("Banned from server."); 01258 return 1; 01259 }
| static int goterror | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 979 of file servmsg.c.
References LOG_MSGS, LOG_SERV, nuke_server(), putlog, and serverror_quit.
00980 { 00981 /* FIXME: fixcolon doesn't do what we need here, this is a temp fix 00982 * fixcolon(msg); 00983 */ 00984 if (msg[0] == ':') 00985 msg++; 00986 putlog(LOG_SERV | LOG_MSGS, "*", "-ERROR from server- %s", msg); 00987 if (serverror_quit) { 00988 putlog(LOG_SERV, "*", "Disconnecting from server."); 00989 nuke_server("Bah, stupid error messages."); 00990 } 00991 return 1; 00992 }
| static int gotfake433 | ( | char * | from | ) | [static] |
Definition at line 45 of file servmsg.c.
References altnick_char, botname, DP_MODE, dprintf, get_altbotnick(), IRC_BOTNICKINUSE, LOG_MISC, nick_len, NULL, putlog, randint, and rfc_casecmp.
Referenced by got433(), and got437().
00046 { 00047 int l = strlen(botname) - 1; 00048 00049 /* First run? */ 00050 if (altnick_char == 0) { 00051 char *alt = get_altbotnick(); 00052 00053 if (alt[0] && (rfc_casecmp(alt, botname))) 00054 /* Alternate nickname defined. Let's try that first. */ 00055 strcpy(botname, alt); 00056 else { 00057 /* Fall back to appending count char. */ 00058 altnick_char = '0'; 00059 if ((l + 1) == nick_len) { 00060 botname[l] = altnick_char; 00061 } else { 00062 botname[++l] = altnick_char; 00063 botname[l + 1] = 0; 00064 } 00065 } 00066 /* No, we already tried the default stuff. Now we'll go through variations 00067 * of the original alternate nick. 00068 */ 00069 } else { 00070 char *oknicks = "^-_\\[]`"; 00071 char *p = strchr(oknicks, altnick_char); 00072 00073 if (p == NULL) { 00074 if (altnick_char == '9') 00075 altnick_char = oknicks[0]; 00076 else 00077 altnick_char = altnick_char + 1; 00078 } else { 00079 p++; 00080 if (!*p) 00081 altnick_char = 'a' + randint(26); 00082 else 00083 altnick_char = (*p); 00084 } 00085 botname[l] = altnick_char; 00086 } 00087 putlog(LOG_MISC, "*", IRC_BOTNICKINUSE, botname); 00088 dprintf(DP_MODE, "NICK %s\n", botname); 00089 return 0; 00090 }
| static int gotkick | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 1194 of file servmsg.c.
References botname, last_time, LOG_SRVOUT, putlog, raw_log, rfc_casecmp, and use_penalties.
01195 { 01196 char *nick; 01197 01198 nick = from; 01199 if (rfc_casecmp(nick, botname)) 01200 /* Not my kick, I don't need to bother about it. */ 01201 return 0; 01202 if (use_penalties) { 01203 last_time += 2; 01204 if (raw_log) 01205 putlog(LOG_SRVOUT, "*", "adding 2secs penalty (successful kick)"); 01206 } 01207 return 0; 01208 }
| static int gotmode | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 1039 of file servmsg.c.
References CHANMETA, check_mode_r, dcc, findanyidx, fixcolon, LOG_JOIN, LOG_MISC, match_my_nick(), newsplit, nuke_server(), NULL, putlog, and serv.
01040 { 01041 char *ch; 01042 01043 ch = newsplit(&msg); 01044 /* Usermode changes? */ 01045 if (strchr(CHANMETA, ch[0]) == NULL) { 01046 if (match_my_nick(ch) && check_mode_r) { 01047 /* umode +r? - D0H dalnet uses it to mean something different */ 01048 fixcolon(msg); 01049 if ((msg[0] == '+') && strchr(msg, 'r')) { 01050 int servidx = findanyidx(serv); 01051 01052 putlog(LOG_MISC | LOG_JOIN, "*", 01053 "%s has me i-lined (jumping)", dcc[servidx].host); 01054 nuke_server("i-lines suck"); 01055 } 01056 } 01057 } 01058 return 0; 01059 }
| static int gotmsg | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 502 of file servmsg.c.
References addignore, answer_ctcp, botnetnick, CHANMETA, check_tcl_ctcp, check_tcl_msg(), check_tcl_msgm(), count_ctcp, ctcp_mode, ctcp_reply, DCC_NOSTRANGERS, DCC_REFUSED, detect_avalanche(), detect_flood(), DP_HELP, dprintf, egg_snprintf, egg_strcasecmp, exclusive_binds, fixcolon, FLOOD_CTCP, FLOOD_PRIVMSG, flud_ctcp_thr, flud_ctcp_time, get_user_by_host, ignore_time, last_ctcp, LOG_MISC, LOG_MODES, LOG_MSGS, LOG_PUBLIC, LOG_SERV, lowercase_ctcp, match_ignore, newsplit, now, NULL, putlog, quiet_reject, rmspace, splitnick, strncpyz, trigger_on_ignore, and UHOSTLEN.
00503 { 00504 char *to, buf[UHOSTLEN], *nick, ctcpbuf[512], *uhost = buf, *ctcp, 00505 *p, *p1, *code; 00506 struct userrec *u; 00507 int ctcp_count = 0; 00508 int ignoring; 00509 00510 /* Notice to a channel, not handled here */ 00511 if (msg[0] && ((strchr(CHANMETA, *msg) != NULL) || (*msg == '@'))) 00512 return 0; 00513 00514 ignoring = match_ignore(from); 00515 to = newsplit(&msg); 00516 fixcolon(msg); 00517 /* Only check if flood-ctcp is active */ 00518 strncpyz(uhost, from, sizeof(buf)); 00519 nick = splitnick(&uhost); 00520 if (flud_ctcp_thr && detect_avalanche(msg)) { 00521 if (!ignoring) { 00522 putlog(LOG_MODES, "*", "Avalanche from %s - ignoring", from); 00523 p = strchr(uhost, '@'); 00524 if (p != NULL) 00525 p++; 00526 else 00527 p = uhost; 00528 egg_snprintf(ctcpbuf, sizeof(ctcpbuf), "*!*@%s", p); 00529 addignore(ctcpbuf, botnetnick, "ctcp avalanche", 00530 now + (60 * ignore_time)); 00531 } 00532 } 00533 /* Check for CTCP: */ 00534 ctcp_reply[0] = 0; 00535 p = strchr(msg, 1); 00536 while ((p != NULL) && (*p)) { 00537 p++; 00538 p1 = p; 00539 while ((*p != 1) && (*p != 0)) 00540 p++; 00541 if (*p == 1) { 00542 *p = 0; 00543 strncpyz(ctcpbuf, p1, sizeof(ctcpbuf)); 00544 ctcp = ctcpbuf; 00545 00546 /* remove the ctcp in msg */ 00547 memmove(p1 - 1, p + 1, strlen(p + 1) + 1); 00548 00549 if (!ignoring) 00550 detect_flood(nick, uhost, from, 00551 strncmp(ctcp, "ACTION ", 7) ? FLOOD_CTCP : FLOOD_PRIVMSG); 00552 /* Respond to the first answer_ctcp */ 00553 p = strchr(msg, 1); 00554 if (ctcp_count < answer_ctcp) { 00555 ctcp_count++; 00556 if (ctcp[0] != ' ') { 00557 code = newsplit(&ctcp); 00558 00559 /* CTCP from oper, don't interpret */ 00560 if ((to[0] == '$') || strchr(to, '.')) { 00561 if (!ignoring) 00562 putlog(LOG_PUBLIC, to, "CTCP %s: %s from %s (%s) to %s", 00563 code, ctcp, nick, uhost, to); 00564 } else { 00565 u = get_user_by_host(from); 00566 if (!ignoring || trigger_on_ignore) { 00567 if (!check_tcl_ctcp(nick, uhost, u, to, code, ctcp) && !ignoring) { 00568 if ((lowercase_ctcp && !egg_strcasecmp(code, "DCC")) || 00569 (!lowercase_ctcp && !strcmp(code, "DCC"))) { 00570 /* If it gets this far unhandled, it means that 00571 * the user is totally unknown. 00572 */ 00573 code = newsplit(&ctcp); 00574 if (!strcmp(code, "CHAT")) { 00575 if (!quiet_reject) { 00576 if (u) 00577 dprintf(DP_HELP, "NOTICE %s :I'm not accepting calls " 00578 "at the moment.\n", nick); 00579 else 00580 dprintf(DP_HELP, "NOTICE %s :%s\n", nick, 00581 DCC_NOSTRANGERS); 00582 } 00583 putlog(LOG_MISC, "*", "%s: %s", DCC_REFUSED, from); 00584 } else 00585 putlog(LOG_MISC, "*", "Refused DCC %s: %s", code, from); 00586 } 00587 } 00588 if (!strcmp(code, "ACTION")) { 00589 putlog(LOG_MSGS, "*", "Action to %s: %s %s", to, nick, ctcp); 00590 } else { 00591 putlog(LOG_MSGS, "*", "CTCP %s: %s from %s (%s)", code, ctcp, 00592 nick, uhost); 00593 } /* I love a good close cascade ;) */ 00594 } 00595 } 00596 } 00597 } 00598 } 00599 } 00600 /* Send out possible ctcp responses */ 00601 if (ctcp_reply[0]) { 00602 if (ctcp_mode != 2) { 00603 dprintf(DP_HELP, "NOTICE %s :%s\n", nick, ctcp_reply); 00604 } else { 00605 if (now - last_ctcp > flud_ctcp_time) { 00606 dprintf(DP_HELP, "NOTICE %s :%s\n", nick, ctcp_reply); 00607 count_ctcp = 1; 00608 } else if (count_ctcp < flud_ctcp_thr) { 00609 dprintf(DP_HELP, "NOTICE %s :%s\n", nick, ctcp_reply); 00610 count_ctcp++; 00611 } 00612 last_ctcp = now; 00613 } 00614 } 00615 if (msg[0]) { 00616 int result = 0; 00617 00618 /* Msg from oper, don't interpret */ 00619 if ((to[0] == '$') || (strchr(to, '.') != NULL)) { 00620 if (!ignoring) { 00621 detect_flood(nick, uhost, from, FLOOD_PRIVMSG); 00622 putlog(LOG_MSGS | LOG_SERV, "*", "[%s!%s to %s] %s", 00623 nick, uhost, to, msg); 00624 } 00625 return 0; 00626 } 00627 00628 detect_flood(nick, uhost, from, FLOOD_PRIVMSG); 00629 u = get_user_by_host(from); 00630 code = newsplit(&msg); 00631 rmspace(msg); 00632 00633 if (!ignoring || trigger_on_ignore) { 00634 result = check_tcl_msgm(code, nick, uhost, u, msg); 00635 00636 if (!result || !exclusive_binds) 00637 if (check_tcl_msg(code, nick, uhost, u, msg)) 00638 return 0; 00639 } 00640 00641 if (!ignoring && result != 2) 00642 putlog(LOG_MSGS, "*", "[%s] %s %s", from, code, msg); 00643 } 00644 return 0; 00645 }
| static int gotnick | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 996 of file servmsg.c.
References altnick, altnick_char, botname, check_queues(), DP_SERVER, dprintf, egg_strcasecmp, fixcolon, get_altbotnick(), IRC_GETALTNICK, IRC_GETORIGNICK, keepnick, LOG_MISC, LOG_SERV, match_my_nick(), nick_juped, NICKLEN, origbotname, putlog, rfc_casecmp, splitnick, and strncpyz.
00997 { 00998 char *nick, *alt = get_altbotnick(); 00999 01000 nick = splitnick(&from); 01001 fixcolon(msg); 01002 check_queues(nick, msg); 01003 if (match_my_nick(nick)) { 01004 /* Regained nick! */ 01005 strncpyz(botname, msg, NICKLEN); 01006 altnick_char = 0; 01007 if (!strcmp(msg, origbotname)) { 01008 putlog(LOG_SERV | LOG_MISC, "*", "Regained nickname '%s'.", msg); 01009 nick_juped = 0; 01010 } else if (alt[0] && !strcmp(msg, alt)) 01011 putlog(LOG_SERV | LOG_MISC, "*", "Regained alternate nickname '%s'.", 01012 msg); 01013 else if (keepnick && strcmp(nick, msg)) { 01014 putlog(LOG_SERV | LOG_MISC, "*", "Nickname changed to '%s'???", msg); 01015 if (!rfc_casecmp(nick, origbotname)) { 01016 putlog(LOG_MISC, "*", IRC_GETORIGNICK, origbotname); 01017 dprintf(DP_SERVER, "NICK %s\n", origbotname); 01018 } else if (alt[0] && !rfc_casecmp(nick, alt) && 01019 egg_strcasecmp(botname, origbotname)) { 01020 putlog(LOG_MISC, "*", IRC_GETALTNICK, alt); 01021 dprintf(DP_SERVER, "NICK %s\n", alt); 01022 } 01023 } else 01024 putlog(LOG_SERV | LOG_MISC, "*", "Nickname changed to '%s'???", msg); 01025 } else if ((keepnick) && (rfc_casecmp(nick, msg))) { 01026 /* Only do the below if there was actual nick change, case doesn't count */ 01027 if (!rfc_casecmp(nick, origbotname)) { 01028 putlog(LOG_MISC, "*", IRC_GETORIGNICK, origbotname); 01029 dprintf(DP_SERVER, "NICK %s\n", origbotname); 01030 } else if (alt[0] && !rfc_casecmp(nick, alt) && 01031 egg_strcasecmp(botname, origbotname)) { 01032 putlog(LOG_MISC, "*", IRC_GETALTNICK, altnick); 01033 dprintf(DP_SERVER, "NICK %s\n", altnick); 01034 } 01035 } 01036 return 0; 01037 }
| static int gotnotice | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 649 of file servmsg.c.
References botname, CHANMETA, check_tcl_ctcr, check_tcl_notc(), detect_avalanche(), detect_flood(), fixcolon, FLOOD_CTCP, FLOOD_NOTICE, flud_ctcp_thr, get_user_by_host, LOG_MODES, LOG_MSGS, LOG_PUBLIC, LOG_SERV, match_ignore, newsplit, NULL, putlog, splitnick, and trigger_on_ignore.
00650 { 00651 char *to, *nick, ctcpbuf[512], *p, *p1, buf[512], *uhost = buf, *ctcp; 00652 struct userrec *u; 00653 int ignoring; 00654 00655 /* Notice to a channel, not handled here */ 00656 if (msg[0] && ((strchr(CHANMETA, *msg) != NULL) || (*msg == '@'))) 00657 return 0; 00658 00659 ignoring = match_ignore(from); 00660 to = newsplit(&msg); 00661 fixcolon(msg); 00662 strcpy(uhost, from); 00663 nick = splitnick(&uhost); 00664 if (flud_ctcp_thr && detect_avalanche(msg)) { 00665 /* Discard -- kick user if it was to the channel */ 00666 if (!ignoring) 00667 putlog(LOG_MODES, "*", "Avalanche from %s", from); 00668 return 0; 00669 } 00670 /* Check for CTCP: */ 00671 p = strchr(msg, 1); 00672 while ((p != NULL) && (*p)) { 00673 p++; 00674 p1 = p; 00675 while ((*p != 1) && (*p != 0)) 00676 p++; 00677 if (*p == 1) { 00678 *p = 0; 00679 ctcp = strcpy(ctcpbuf, p1); 00680 strcpy(p1 - 1, p + 1); 00681 if (!ignoring) 00682 detect_flood(nick, uhost, from, FLOOD_CTCP); 00683 p = strchr(msg, 1); 00684 if (ctcp[0] != ' ') { 00685 char *code = newsplit(&ctcp); 00686 00687 /* CTCP reply from oper, don't interpret */ 00688 if ((to[0] == '$') || strchr(to, '.')) { 00689 if (!ignoring) 00690 putlog(LOG_PUBLIC, "*", 00691 "CTCP reply %s: %s from %s (%s) to %s", code, ctcp, 00692 nick, uhost, to); 00693 } else { 00694 u = get_user_by_host(from); 00695 if (!ignoring || trigger_on_ignore) { 00696 check_tcl_ctcr(nick, uhost, u, to, code, ctcp); 00697 if (!ignoring) 00698 /* Who cares? */ 00699 putlog(LOG_MSGS, "*", 00700 "CTCP reply %s: %s from %s (%s) to %s", 00701 code, ctcp, nick, uhost, to); 00702 } 00703 } 00704 } 00705 } 00706 } 00707 if (msg[0]) { 00708 00709 /* Notice from oper, don't interpret */ 00710 if ((to[0] == '$') || (strchr(to, '.') != NULL)) { 00711 if (!ignoring) { 00712 detect_flood(nick, uhost, from, FLOOD_NOTICE); 00713 putlog(LOG_MSGS | LOG_SERV, "*", "-%s (%s) to %s- %s", 00714 nick, uhost, to, msg); 00715 } 00716 return 0; 00717 } 00718 00719 /* Server notice? */ 00720 if ((nick[0] == 0) || (uhost[0] == 0)) { 00721 00722 /* Hidden `250' connection count message from server */ 00723 if (strncmp(msg, "Highest connection count:", 25)) 00724 putlog(LOG_SERV, "*", "-NOTICE- %s", msg); 00725 00726 return 0; 00727 } 00728 00729 detect_flood(nick, uhost, from, FLOOD_NOTICE); 00730 u = get_user_by_host(from); 00731 00732 if (!ignoring || trigger_on_ignore) 00733 if (check_tcl_notc(nick, uhost, u, botname, msg) == 2) 00734 return 0; 00735 00736 if (!ignoring) 00737 putlog(LOG_MSGS, "*", "-%s (%s)- %s", nick, uhost, msg); 00738 } 00739 return 0; 00740 }
| static int gotping | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
| static int gotpong | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 832 of file servmsg.c.
References fixcolon, lastpingtime, my_atoul, newsplit, now, and server_lag.
00833 { 00834 newsplit(&msg); 00835 fixcolon(msg); /* Scrap server name */ 00836 server_lag = now - my_atoul(msg); 00837 if (server_lag > 99999) { 00838 /* IRCnet lagmeter support by drummer */ 00839 server_lag = now - lastpingtime; 00840 } 00841 return 0; 00842 }
| static int gotwall | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 772 of file servmsg.c.
References check_tcl_wall(), fixcolon, LOG_WALL, putlog, and splitnick.
00773 { 00774 char *nick; 00775 00776 fixcolon(msg); 00777 00778 if (check_tcl_wall(from, msg) != 2) { 00779 if (strchr(from, '!')) { 00780 nick = splitnick(&from); 00781 putlog(LOG_WALL, "*", "!%s(%s)! %s", nick, from, msg); 00782 } else 00783 putlog(LOG_WALL, "*", "!%s! %s", from, msg); 00784 } 00785 return 0; 00786 }
| static void kill_server | ( | int | idx, | |
| void * | x | |||
| ) | [static] |
Definition at line 1090 of file servmsg.c.
References CHANNEL_CLEAR, chanset, disconnect_server(), _module_entry::funcs, module_find, and chanset_t::next.
01091 { 01092 module_entry *me; 01093 01094 disconnect_server(idx); 01095 if ((me = module_find("channels", 0, 0)) && me->funcs) { 01096 struct chanset_t *chan; 01097 01098 for (chan = chanset; chan; chan = chan->next) 01099 (me->funcs[CHANNEL_CLEAR]) (chan, 1); 01100 } 01101 /* A new server connection will be automatically initiated in 01102 * about 2 seconds. */ 01103 }
| static int match_my_nick | ( | char * | nick | ) | [static] |
Definition at line 294 of file servmsg.c.
References botname, and rfc_casecmp.
Referenced by check_expired_chanstuff(), check_lonely_channel(), check_this_member(), cmd_dehalfop(), cmd_deop(), cmd_kick(), cmd_kickban(), detect_chan_flood(), detect_flood(), got311(), got352or4(), got_ban(), got_dehalfop(), got_deop(), got_exempt(), got_halfop(), got_invite(), got_key(), got_op(), gotjoin(), gotkick(), gotmode(), gotnick(), gotpart(), kick_all(), maybe_revenge(), msg_addhost(), msg_die(), msg_go(), msg_halfop(), msg_hello(), msg_help(), msg_ident(), msg_info(), msg_invite(), msg_jump(), msg_key(), msg_memory(), msg_op(), msg_pass(), msg_rehash(), msg_reset(), msg_save(), msg_status(), msg_voice(), msg_who(), msg_whois(), recheck_channel(), and want_to_revenge().
00295 { 00296 if (!rfc_casecmp(nick, botname)) 00297 return 1; 00298 return 0; 00299 }
| static void minutely_checks | ( | ) | [static] |
Definition at line 791 of file servmsg.c.
References botname, chanset_t::channel, channel_active, chanset, count, DP_SERVER, dprintf, egg_strcasecmp, get_altbotnick(), keepnick, chan_t::members, min_servs, chanset_t::next, origbotname, and server_online.
Referenced by server_close(), and server_start().
00792 { 00793 char *alt; 00794 static int count = 4; 00795 int ok = 0; 00796 struct chanset_t *chan; 00797 00798 /* Only check if we have already successfully logged in. */ 00799 if (!server_online) 00800 return; 00801 if (keepnick) { 00802 /* NOTE: now that botname can but upto NICKLEN bytes long, 00803 * check that it's not just a truncation of the full nick. 00804 */ 00805 if (strncmp(botname, origbotname, strlen(botname))) { 00806 /* See if my nickname is in use and if if my nick is right. */ 00807 alt = get_altbotnick(); 00808 if (alt[0] && egg_strcasecmp(botname, alt)) 00809 dprintf(DP_SERVER, "ISON :%s %s %s\n", botname, origbotname, alt); 00810 else 00811 dprintf(DP_SERVER, "ISON :%s %s\n", botname, origbotname); 00812 } 00813 } 00814 if (min_servs == 0) 00815 return; 00816 for (chan = chanset; chan; chan = chan->next) 00817 if (channel_active(chan) && chan->channel.members == 1) { 00818 ok = 1; 00819 break; 00820 } 00821 if (!ok) 00822 return; 00823 count++; 00824 if (count >= 5) { 00825 dprintf(DP_SERVER, "LUSERS\n"); 00826 count = 0; 00827 } 00828 }

| static void nuke_server | ( | char * | reason | ) | [static] |
Definition at line 391 of file servmsg.c.
References disconnect_server(), dprintf, findanyidx, lostdcc, and serv.
Referenced by cmd_jump(), got251(), got451(), got465(), goterror(), gotmode(), msg_die(), msg_jump(), server_close(), and server_die().
00392 { 00393 if (serv >= 0) { 00394 int servidx = findanyidx(serv); 00395 00396 if (reason && (servidx > 0)) 00397 dprintf(servidx, "QUIT :%s\n", reason); 00398 disconnect_server(servidx); 00399 lostdcc(servidx); 00400 } 00401 }
| static void server_activity | ( | int | idx, | |
| char * | msg, | |||
| int | len | |||
| ) | [static] |
Definition at line 1127 of file servmsg.c.
References check_tcl_raw(), check_tcl_raw4(), dcc, from, lastpingcheck, LOG_RAW, LOG_SERV, match_ignore, newsplit, putlog, raw_log, dcc_table::timeout_val, and trying_server.
01128 { 01129 char *from, *code, *tags, *new_from, *new_code, *new_msg; 01130 01131 if (trying_server) { 01132 strcpy(dcc[idx].nick, "(server)"); 01133 putlog(LOG_SERV, "*", "Connected to %s", dcc[idx].host); 01134 trying_server = 0; 01135 SERVER_SOCKET.timeout_val = 0; 01136 } 01137 lastpingcheck = 0; 01138 tags = ""; 01139 if (msg[0] == '@') { 01140 msg++; 01141 tags = newsplit(&msg); 01142 putlog(LOG_RAW, "*", "[v3] %s", tags); 01143 } 01144 from = ""; 01145 if (msg[0] == ':') { 01146 msg++; 01147 from = newsplit(&msg); 01148 } 01149 code = newsplit(&msg); 01150 new_from = ""; 01151 new_code = ""; 01152 if (strcmp(tags, "") != 0 && strcmp(code, "PRIVMSG") == 0) { 01153 new_from = from; 01154 new_code = "PRIVMSGV3"; 01155 putlog(LOG_RAW, "*", "[v3] TAGS '%s' - '%s'", tags, code); 01156 //simple_sprintf(new_msg, "%s %s", tags, msg); 01157 new_msg = msg; 01158 } 01159 if (raw_log && ((strcmp(code, "PRIVMSG") && strcmp(code, "NOTICE")) || 01160 !match_ignore(from))) { 01161 if (!strcmp(from, "")) 01162 putlog(LOG_RAW, "*", "[@] %s %s", code, msg); 01163 else 01164 putlog(LOG_RAW, "*", "[@] %s %s %s", from, code, msg); 01165 } 01166 /* This has GOT to go into the raw binding table, * merely because this 01167 * is less effecient. 01168 */ 01169 check_tcl_raw(from, code, msg); 01170 01171 //putlog(LOG_RAW, "*", "[v3] Derp1?"); 01172 if (strcmp(tags, "") != 0 && strcmp(new_code, "PRIVMSGV3") == 0) { 01173 //putlog(LOG_RAW, "*", "[v3] Derp2?"); 01174 if (raw_log && !match_ignore(new_from)) { 01175 if (!strcmp(new_from, "")) 01176 putlog(LOG_RAW, "*", "[@v3] %s %s", new_code, new_msg); 01177 else 01178 putlog(LOG_RAW, "*", "[@v3] %s %s %s", new_from, new_code, new_msg); 01179 } 01180 //putlog(LOG_RAW, "*", "[v3] Derp3?"); 01181 check_tcl_raw4(new_from, new_code, new_msg, tags); 01182 //putlog(LOG_RAW, "*", "[v3] Derp4?"); 01183 } 01184 //putlog(LOG_RAW, "*", "[v3] Derp END?"); 01185 }
| static void server_resolve_failure | ( | int | servidx | ) | [static] |
Definition at line 1380 of file servmsg.c.
References dcc, IRC_DNSFAILED, IRC_FAILEDCONNECT, LOG_SERV, lostdcc, putlog, resolvserv, and serv.
01381 { 01382 serv = -1; 01383 resolvserv = 0; 01384 putlog(LOG_SERV, "*", "%s %s (%s)", IRC_FAILEDCONNECT, dcc[servidx].host, 01385 IRC_DNSFAILED); 01386 lostdcc(servidx); 01387 }
| static void server_resolve_success | ( | int | servidx | ) | [static] |
Definition at line 1389 of file servmsg.c.
References altnick_char, botname, botrealname, botuser, changeover_dcc, curserv, dcc, DP_MODE, dprintf, fatal, iptostr, IRC_FAILEDCONNECT, LOG_SERV, lostdcc, neterror, never_give_up, now, open_telnet, origbotname, server_list::pass, server_list::port, putlog, resolvserv, rmspace, serv, server_timeout, and dcc_table::timeout_val.
01390 { 01391 int oldserv = dcc[servidx].u.dns->ibuf; 01392 char s[121], pass[121]; 01393 01394 resolvserv = 0; 01395 dcc[servidx].addr = dcc[servidx].u.dns->ip; 01396 strcpy(pass, dcc[servidx].u.dns->cbuf); 01397 changeover_dcc(servidx, &SERVER_SOCKET, 0); 01398 serv = open_telnet(iptostr(htonl(dcc[servidx].addr)), dcc[servidx].port); 01399 if (serv < 0) { 01400 neterror(s); 01401 putlog(LOG_SERV, "*", "%s %s (%s)", IRC_FAILEDCONNECT, dcc[servidx].host, 01402 s); 01403 lostdcc(servidx); 01404 if (oldserv == curserv && !never_give_up) 01405 fatal("NO SERVERS WILL ACCEPT MY CONNECTION.", 0); 01406 } else { 01407 dcc[servidx].sock = serv; 01408 /* Queue standard login */ 01409 dcc[servidx].timeval = now; 01410 SERVER_SOCKET.timeout_val = &server_timeout; 01411 /* Another server may have truncated it, so use the original */ 01412 strcpy(botname, origbotname); 01413 /* Start alternate nicks from the beginning */ 01414 altnick_char = 0; 01415 if (pass[0]) 01416 dprintf(DP_MODE, "PASS %s\n", pass); 01417 dprintf(DP_MODE, "NICK %s\n", botname); 01418 01419 rmspace(botrealname); 01420 if (botrealname[0] == 0) 01421 strcpy(botrealname, "/msg LamestBot hello"); 01422 dprintf(DP_MODE, "USER %s . . :%s\n", botuser, botrealname); 01423 01424 /* Wait for async result now. */ 01425 } 01426 }
| static void timeout_server | ( | int | idx | ) | [static] |
| static int whoispenalty | ( | char * | from, | |
| char * | msg | |||
| ) | [static] |
Definition at line 1212 of file servmsg.c.
References egg_strcasecmp, last_time, LOG_SRVOUT, putlog, raw_log, realservername, and use_penalties.
01213 { 01214 if (realservername && use_penalties && 01215 egg_strcasecmp(from, realservername)) { 01216 01217 last_time += 1; 01218 01219 if (raw_log) 01220 putlog(LOG_SRVOUT, "*", "adding 1sec penalty (remote whois)"); 01221 } 01222 01223 return 0; 01224 }
Variable Documentation
char altnick_char = 0 [static] |
Definition at line 28 of file servmsg.c.
Referenced by got001(), gotfake433(), gotnick(), and server_resolve_success().
int count_ctcp = 0 [static] |
char ctcp_reply[1024] = "" [static] |
Definition at line 403 of file servmsg.c.
Referenced by ctcp_CHAT(), ctcp_CLIENTINFO(), ctcp_ECHOERR(), ctcp_FINGER(), ctcp_PING(), ctcp_TIME(), ctcp_USERINFO(), ctcp_VERSION(), and gotmsg().
char lastmsghost[3][81] [static] |
Definition at line 406 of file servmsg.c.
Referenced by detect_flood().
int lastmsgs[3] [static] |
Definition at line 405 of file servmsg.c.
Referenced by detect_flood().
time_t lastmsgtime[3] [static] |
Definition at line 407 of file servmsg.c.
Referenced by detect_flood().
cmd_t my_raw_binds[] [static] |
{
{"PRIVMSG", "", (IntFunc) gotmsg, 0 },
{"NOTICE", "", (IntFunc) gotnotice, 0 },
{"MODE", "", (IntFunc) gotmode, 0 },
{"PING", "", (IntFunc) gotping, 0 },
{"PONG", "", (IntFunc) gotpong, 0 },
{"WALLOPS", "", (IntFunc) gotwall, 0 },
{"001", "", (IntFunc) got001, 0 },
{"251", "", (IntFunc) got251, 0 },
{"303", "", (IntFunc) got303, 0 },
{"432", "", (IntFunc) got432, 0 },
{"433", "", (IntFunc) got433, 0 },
{"437", "", (IntFunc) got437, 0 },
{"438", "", (IntFunc) got438, 0 },
{"451", "", (IntFunc) got451, 0 },
{"442", "", (IntFunc) got442, 0 },
{"465", "", (IntFunc) got465, 0 },
{"NICK", "", (IntFunc) gotnick, 0 },
{"ERROR", "", (IntFunc) goterror, 0 },
{"ERROR:", "", (IntFunc) goterror, 0 },
{"KICK", "", (IntFunc) gotkick, 0 },
{"318", "", (IntFunc) whoispenalty, 0 },
{"311", "", (IntFunc) got311, 0 },
{ 0 , 0 , 0 , 0 }
}
Definition at line 1262 of file servmsg.c.
Referenced by server_close(), and server_start().
struct dcc_table SERVER_SOCKET [static] |
{
"SERVER",
0,
eof_server,
server_activity,
0 ,
timeout_server,
display_server,
0 ,
kill_server,
0
}
 1.6.1
1.6.1